CSE306: Computer Networks
Module 1 : Introduction to Networking
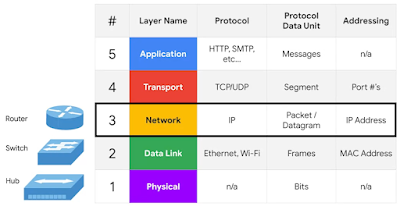
⭐TCP/IP Five Layer Network Model:
1. Physical Layer
- Definition: Represents the physical hardware used to interconnect devices.
- Components:
- Cables: Specifications for networking cables.
- Connectors: Types and standards for connectors joining devices.
- Signals: Specifications for how signals are sent over connections.
- Purpose: Establishes the physical means of data transmission between devices.
2. Data Link Layer
- Alternate Names: Network Interface Layer, Network Access Layer.
- Function: Provides a common way to interpret signals so that devices can communicate over a single link.
- Key Protocols:
- Ethernet: Most common protocol for wired networks.
- Wireless Technologies: Increasingly popular for network access.
- Purpose: Manages the transmission of data over a single network link and handles addressing at this local level.
3. Network Layer
- Alternate Name: Internet Layer.
- Function: Facilitates communication between different networks through routers.
- Key Protocol:
- IP (Internet Protocol): Central to the internet and most small networks, responsible for addressing and routing data.
- Purpose: Ensures data is delivered across multiple networks, from one node to another over the internet or other interconnected networks.
4. Transport Layer
- Function: Ensures that data is delivered to the correct application processes on a node.
- Key Protocols:
- TCP (Transmission Control Protocol): Provides reliable data delivery by ensuring data is received correctly and in the correct order.
- UDP (User Datagram Protocol): Offers faster, but less reliable, data delivery compared to TCP.
- Purpose: Manages end-to-end communication, error checking, and data recovery between applications on different nodes.
5. Application Layer
- Function: Provides protocols directly used by applications to communicate over the network.
- Common Protocols:
- HTTP/HTTPS: For web browsing.
- SMTP/IMAP/POP3: For email transmission and retrieval.
- Purpose: Enables user-level interactions with network services and applications, such as sending emails or browsing websites.
Analogies for Understanding the Layers:
- Physical Layer: Delivery truck and roads.
- Data Link Layer: How the truck navigates from one intersection to the next.
- Network Layer: Deciding which roads to take to reach the destination.
- Transport Layer: Ensuring the delivery driver knows how to deliver the package and notify the recipient.
- Application Layer: The actual contents of the package being delivered.
⭐Overview of the OSI Networking Model:
- Definition: A seven-layer model used to understand and describe network protocols and interactions.
- Application: Commonly used in many networking certifications (e.g., Net+, Cisco certifications).
Comparison with the TCP/IP Five Layer Model
TCP/IP Model:
- Layers: Physical, Data Link, Network, Transport, Application.
- Differences: Combines the functionalities of the OSI's Physical and Data Link layers into a single layer.
OSI Model:
- Layers: Divides functionalities into seven distinct layers, including:
- Physical Layer (same as TCP/IP's Physical Layer).
- Data Link Layer (same as TCP/IP's Data Link Layer).
- Network Layer (same as TCP/IP's Network Layer).
- Transport Layer (same as TCP/IP's Transport Layer).
- Session Layer (not explicitly defined in TCP/IP; handled by Transport Layer).
- Presentation Layer (not explicitly defined in TCP/IP; typically part of Application Layer).
- Application Layer (encompasses higher-level functions in TCP/IP's Application Layer).
- Layers: Divides functionalities into seven distinct layers, including:
⭐The Basic of Networking Devices:
1) Cables:
- Purpose: Connect devices and enable data transmission between them.
- Categories:
- Copper Cables: Most common, used in various networking scenarios.
- Fiber Optic Cables: Specialized for high-speed and long-distance data transmission.
Copper Cables
General Characteristics:
- Construction: Multiple pairs of copper wires inside a plastic insulator.
- Data Transmission: Uses voltage changes to represent binary data (ones and zeros).
Types of Copper Twisted Pair Cables:
Cat5 (Category 5):
- Status: Older standard, largely replaced by Cat5e and Cat6.
- Characteristics: Basic twisted pair arrangement, limited speed and distance.
Cat5e (Category 5 Enhanced):
- Improvements: Enhanced to reduce crosstalk (interference between wires).
- Performance: Improved data transfer rates and reliability compared to Cat5.
- Usage: More common in modern networks due to better performance.
Cat6 (Category 6):
- Improvements: Higher specifications for reducing crosstalk and interference.
- Performance: Faster data transfer and more reliable than Cat5e.
- Limitations: Shorter maximum distance at higher speeds due to stricter internal arrangements.
- Cost: Generally more expensive due to advanced specifications.
Crosstalk:
- Definition: Electrical pulses from one wire are unintentionally detected by another wire.
- Impact: Can cause data errors and retransmissions, slowing down network performance.
- Mitigation: Enhanced cables like Cat5e and Cat6 reduce crosstalk, improving data transfer efficiency.
Fiber Optic Cables
General Characteristics:
- Construction: Tiny glass tubes (optical fibers) about the width of a human hair.
- Data Transmission: Uses light pulses instead of electrical signals to represent binary data.
Advantages:
- Speed: Generally faster data transmission compared to copper cables.
- Distance: Can transmit data over much longer distances without significant data loss.
- Interference: Immune to electromagnetic interference, making them ideal for environments with high interference.
Disadvantages:
- Cost: More expensive than copper cables.
- Fragility: More delicate and can be damaged more easily than copper cables.
- Usage: Common in data centers and long-distance communication rather than in typical office or home settings.
2) Hubs and Switches:
Hubs
- Definition: A network device that connects multiple computers in a network segment, allowing them to communicate with each other.
- Layer: Physical Layer (Layer 1).
- Function:
- Broadcasting: Receives incoming data and broadcasts it to all connected devices.
- Data Handling: Each device connected to the hub must determine if the data is intended for it or if it should be ignored.
- Collision Domain:
- Definition: A network segment where multiple devices share the same communication channel.
- Issue: When multiple devices send data simultaneously, their signals can collide, causing interference.
- Impact: Results in retransmissions and delays as devices must wait for a clear channel.
- Current Use:
- Historical: Hubs are largely considered obsolete due to their inefficiency and the prevalence of more advanced devices like switches.
- Limitations: Increased network noise and collisions due to broadcast nature and lack of data filtering.
Switches
- Definition: A network device that connects multiple computers and manages data traffic more efficiently than a hub.
- Layer: Data Link Layer (Layer 2).
- Function:
- Data Inspection: Analyzes the Ethernet frame data to determine the intended recipient.
- Selective Forwarding: Sends data only to the specific device for which it is intended, not to all devices.
- Collision Domain:
- Reduction: Switches segment the network into smaller collision domains by forwarding data only to the intended recipient.
- Advantage: Minimizes collisions and reduces the need for retransmissions, leading to more efficient data transfer.
- Performance:
- Throughput: Higher overall throughput compared to hubs due to reduced collisions and more efficient data handling.
- Scalability: Better suited for modern networks with higher performance and reliability needs.
3) Routers:
- Definition: A device that forwards data between independent networks, enabling communication across different networks.
- Layer: Network Layer (Layer 3).
Functionality
- Data Inspection:
- IP Data: Routers inspect IP packets to determine the best path for forwarding data.
- Routing Tables: Routers maintain internal tables with information about how to route traffic between various networks.
Types of Routers
Home or Small Office Routers:
- Purpose:
- Traffic Handling: Forward traffic from the local network (LAN) to the Internet Service Provider (ISP).
- Routing Tables: Generally have simpler and less detailed routing tables compared to core routers.
- Function: Connects internal devices to the internet and manages local network traffic.
- Purpose:
Core Routers:
- Purpose:
- Internet Backbone: Form the backbone of the internet, handling vast amounts of traffic between different networks.
- Routing Tables: Feature complex and detailed routing tables to manage and route traffic efficiently.
- Function:
- High Traffic Handling: Manage large volumes of data and numerous connections to other routers.
- Complex Routing: Make sophisticated routing decisions based on network topology and traffic conditions.
Routing Protocols
- BGP (Border Gateway Protocol):
- Function:
- Data Sharing: Allows routers to exchange information about network routes.
- Optimal Paths: Helps routers learn and select the most efficient paths for forwarding data.
- Usage: Essential for managing how data is routed across the global internet.
- Function:
Network Traffic
- Path Complexity:
- Data Transmission: Data sent from a web browser to a web server may traverse numerous routers and networks.
- Internet Scale: The internet is vast and complex, with routers playing a crucial role in directing traffic to its destination.
4) Servers and Clients:
Basic Concepts
Server:
- Definition: A node or computer program that provides data or services to other nodes or programs (clients) upon request.
- Function:
- Data Provision: Delivers data or resources such as files, webpages, or application services.
- Role: Its primary purpose is to serve data or resources to clients.
Client:
- Definition: A node or computer program that requests data or services from a server.
- Function:
- Data Request: Initiates requests for data or services from servers.
- Role: Its primary purpose is to access and use the data or resources provided by servers.
Key Points
Nodes as Servers and Clients:
- Dual Role: Nodes can act as both servers and clients depending on the context and the services being provided or requested.
- Examples:
- Email Server: Provides email services to clients (e.g., email applications). However, it may act as a client when it queries a DNS server for domain resolution.
- Desktop Computer: Typically functions as a client when accessing web services, but can act as a server when sharing files or resources with other computers.
Computer Programs as Servers and Clients:
- Server Programs: Software running on a node that provides services or data (e.g., a web server serving webpages).
- Client Programs: Software that requests services or data (e.g., a web browser requesting webpages).
Primary vs. Secondary Roles:
- Primary Role:
- Server: The main function is to provide data or services.
- Client: The main function is to request and use data or services.
- Secondary Role:
- A server might occasionally act as a client (e.g., querying a DNS server).
- A client might occasionally act as a server (e.g., sharing files with other computers).
- Primary Role:
Network Topologies
Server-Centric Topologies:
- Purpose: Nodes are typically designated as servers or clients based on their primary function in the network.
- Example: In a corporate network, file servers provide data to client computers, which are primarily used for accessing and using that data.
Client-Centric Topologies:
- Purpose: Nodes act as clients by default but may perform server functions as needed.
- Example: In a peer-to-peer network, each computer can act as both a client and a server, depending on whether it is providing or requesting data.
⭐The Physical Layer:
1) Moving Bits Across The Wire:
Physical Layer Overview
- Focus: Transmitting raw bits (ones and zeros) across network links.
- Complexity: Involves intricate mathematics, physics, and electrical engineering principles, but key concepts for IT support are more approachable.
Basic Concepts
- Bit:
- Definition: The smallest unit of data, representing either a 1 or a 0.
- Role: All data transmitted over networks, including frames and packets, are ultimately composed of these bits.
Transmission Methods
Copper Network Cables:
- Structure: Consist of multiple pairs of copper wires.
- Function: Carry a constant electrical charge when connected to devices on both ends.
Modulation:
- Definition: The process of varying the voltage of the electrical charge on the cable to represent binary data.
- Purpose: Converts binary data into a form that can be transmitted over the network.
Line Coding:
- Definition: A specific type of modulation used in computer networks.
- Function: Encodes binary data into voltage levels so that devices on either end of the cable can interpret them as ones and zeros.
Data Transmission
- Efficiency:
- Speed: Modern networks can transmit up to 10 billion bits per second over a single network cable.
- Volume: High-speed data transmission enables activities like streaming, emailing, and accessing ATM networks to occur efficiently.
2) Twisted Pair Cabling And Duplexing:
Twisted Pair Cabling
Definition: A type of networking cable that consists of pairs of copper wires twisted together.
Purpose:
- Interference Protection: Twisting helps shield the signals from electromagnetic interference (EMI) and reduces cross-talk between neighboring pairs.
- Signal Integrity: Maintains the quality and consistency of the transmitted signals.
Common Types:
- Cat5e: An enhanced version of Cat5, with improved specifications for reduced crosstalk and better performance.
- Cat6: Higher specification than Cat5e, designed to support higher speeds and frequencies, and has stricter standards to further reduce crosstalk.
Construction:
- Wires: Typically includes eight wires organized into four twisted pairs.
- Jacket: The outer layer encases all the twisted pairs for physical protection and insulation.
Duplexing
- Definition: The ability of a network to handle data transmission in both directions.
- Types:
Full Duplex:
- Description: Allows simultaneous communication in both directions.
- Implementation: Uses separate pairs of wires for transmitting and receiving data.
- Advantage: Enables devices to send and receive data at the same time, leading to efficient and faster communication.
Half Duplex:
- Description: Allows communication in both directions but not simultaneously.
- Implementation: Uses the same pairs of wires for both transmitting and receiving data, but only one direction of data flow occurs at a time.
- Disadvantage: Communication can be less efficient as only one device can transmit data at any given moment, potentially causing delays or reduced throughput.
Key Points
Twisted Pair Cable Structure:
- Pairs: Four twisted pairs within a standard Cat6 cable.
- Usage: The number of active pairs can vary depending on the technology (e.g., some Ethernet standards use all four pairs, while others might use only two pairs).
Duplex Communication:
- Full Duplex: Ideal for high-speed and efficient network performance, commonly used in modern networks.
- Half Duplex: Often used in older systems or simpler network setups where simultaneous two-way communication is not necessary.
Impact of Issues:
- Connection Degradation: If a network link reports as half-duplex, it indicates potential issues such as hardware faults or misconfigurations that limit communication efficiency.
3) Network Ports and Patch Panels:
The physical layer of networking involves not just the cables and connectors but also the network ports and patch panels that facilitate the final steps of network connectivity. Understanding these components is crucial for troubleshooting and setting up network environments.
Network Ports
RJ-45 Connectors:
- RJ-45 (Registered Jack 45) is the most common type of plug used in Ethernet networks. It is a modular connector with eight pins, corresponding to the eight wires in a twisted pair cable.
- Usage: RJ-45 connectors are used to connect network cables to network ports on various devices such as switches, routers, and network interface cards (NICs).
Network Ports:
- Definition: Network ports are the physical sockets on networking devices where Ethernet cables are plugged in.
- Types and Quantity:
- Switches: Typically have multiple ports (e.g., 24, 48) to connect many devices.
- Servers and Desktops: Generally have one or two network ports.
- Laptops, Tablets, Phones: May not have Ethernet ports, relying instead on Wi-Fi.
LED Indicators:
- Link Light:
- Function: Indicates whether a cable is properly connected and whether both devices at either end are powered on.
- Status: Lit when a good connection is established.
- Activity Light:
- Function: Shows data transmission across the cable.
- Status: Flashing indicates active data transfer, though with high-speed networks, it may not reflect the exact data activity.
- Link Light:
Advanced Indicators:
- Switches: May use LEDs for additional statuses such as link speed or errors. Always refer to the hardware documentation to understand what each light indicates.
Patch Panels
- Definition:
- A patch panel is a hardware device that consolidates multiple network cables into a single unit. It provides a central location for cable termination and management.
- Functionality:
- Connection Point: Patch panels allow for easy organization and management of network cables. Each port on the patch panel corresponds to a cable run that connects to various endpoints (e.g., offices, workstations).
- Integration: Cables from the patch panel are usually connected to network switches or routers to provide network access throughout a building or data center.
- Setup:
- Cable Runs: Cables are run through walls or conduits to reach the patch panel.
- Port Identification: Each port on a patch panel is labeled to correspond with specific locations in the network, making troubleshooting and reconfiguration easier.
⭐Cabling Tools:
Crimper
- Description:
- A crimper resembles a pair of pliers and is used to attach connectors to the ends of network cables.
- Function:
- Crimping: The tool presses the metal pins of a connector into the conductors of the cable, ensuring a secure electrical connection.
- Usage:
- Commonly used with RJ-45 connectors for Ethernet cables.
- Essential for creating custom-length cables and making sure connectors are properly attached.
Cable Stripper
- Description:
- Similar in appearance to pliers, a cable stripper has a set of blades designed to remove the outer insulation of cables without damaging the internal wires.
- Function:
- Insulation Removal: Strips the protective rubber or plastic coating from network cables, exposing the inner wires for crimping or termination.
- Usage:
- Used before crimping cables to ensure proper connection.
Wi-Fi Analyzer
- Description:
- A handheld or software-based tool that scans and analyzes Wi-Fi signals in a given area.
- Function:
- Signal Analysis: Measures signal strength, channel utilization, and interference to help optimize Wi-Fi performance.
- Data Collection: Provides insights into the quality of the wireless network and potential sources of interference.
- Usage:
- Useful for diagnosing Wi-Fi connectivity issues and optimizing network performance.
Toner Probe
- Description:
- Consists of two parts: a tone generator and a probe. The tone generator is plugged into a cable, and the probe is used to detect the tone.
- Function:
- Cable Tracing: The probe emits a tone that gets louder as it nears the cable connected to the tone generator.
- Usage:
- Helps locate and identify network cables, especially in large installations or when cables are not clearly labeled.
Punch Down Tool
- Description:
- A hand tool used for inserting wires into punch-down blocks or jacks.
- Function:
- Wiring Termination: Pushes wires into the connectors on a punch-down panel or keystone jack, ensuring a secure connection.
- Usage:
- Essential for terminating cables into patch panels, wall jacks, and other network hardware.
Cable Tester
- Description:
- An electronic device used to test the integrity of network cables.
- Function:
- Parameters Tested: Measures attenuation, impedance, noise, near-end crosstalk, attenuation-to-crosstalk ratio (ACR), and PowerSum NEXT.
- Integrity Check: Ensures cables meet cabling standards and perform correctly.
- Usage:
- Used for testing newly installed cables or troubleshooting issues to ensure proper network performance.
Loopback Plug
- Description:
- A simple device that loops network traffic back to the port after it is received.
- Function:
- Port Testing: Tests the functionality of network ports by sending data out and receiving it back.
- Usage:
- Useful for diagnosing port issues and ensuring ports are operational.
Network Tap
- Description:
- An external device that creates a copy of network traffic for monitoring and analysis.
- Function:
- Traffic Monitoring: Copies all traffic between two points in the network, allowing monitoring devices to analyze it without interrupting the network flow.
- Usage:
- Employed in network monitoring and analysis to capture traffic for security and performance evaluations.
⭐Ethernet Over Twisted Pair Technologies:
Overview
Importance: Ethernet over twisted pair technologies is crucial for establishing network connections in both business and home environments. This method of connection typically starts with an internet service delivered through coaxial or fiber-optic cables, which then interfaces with a gateway modem. The modem connects to internal devices or a router via twisted pair Ethernet cables (CAT cables), which distribute network connections.
Applications: Ethernet over twisted pair cables can also provide telephone and television services in addition to data networking.
Twisted Pair Cables
Historical Context:
- Early Configurations: Initially, telephone and early data cables used two parallel copper wires, leading to issues with electromagnetic interference (EMI), radio frequency interference (RFI), and crosstalk.
- Improvement: Twisting the pairs together significantly mitigated these interference issues.
Advantages of Twisted Pair Ethernet Cables:
- Interference Protection: Provides protection against EMI, RFI, and crosstalk.
- Cost and Accessibility: Low-cost options make it accessible for home users and small businesses.
- Physical Properties: Thin, lightweight, and flexible, making installation and movement easy.
- Suitable Range: Effective for short-distance connections within buildings and homes.
- Versatility: Supports both data and voice/telephone communications.
Types of Twisted Pair Ethernet Cables
Unshielded Twisted Pair (UTP):
- Description: The most common and least expensive type.
- Protection: Basic protection against EMI, RFI, and crosstalk.
- Usage: Widely used in standard business and home networks.
Shielded Twisted Pair (STP):
- Description: Used in environments with significant EMI, RFI, or crosstalk issues.
- Protection: Features braided aluminum or copper shielding around the twisted pairs.
- Usage: Suitable for environments with higher levels of interference.
Foiled Twisted Pair (FTP):
- Description: Provides shielding against EMI, RFI, and crosstalk.
- Protection: Uses a thin foil shield around the bundle of twisted pairs.
- Usage: Effective in environments with moderate to high interference.
- Hybrid Options:
- Combination Shields: STP and FTP shields can be combined in the same cable or applied to individual twisted pairs for extra protection.
- Shielded with Foiled Twisted Pair (SF/FTP): Combines braided and foil shielding for maximum protection, often used in industrial environments with high interference.
Straight-through Cable
Description: Also known as patch cables, these are the primary Ethernet cables used in networks.
Usage:
- Typical Connections: Connects computers and routers to hubs, switches, or other networking devices. Also used to connect servers to switches.
Identification:
- Color Code: Both ends of a straight-through cable have the same color and stripe order for twisted pairs.
- Pin Configuration:
- Pins 1 & 2: Orange wires for sending data.
- Pins 3 & 6: Green wires for receiving data.
- 100Base-T Networks: Do not use blue and brown wires.
- Gigabit Ethernet: May include blue and brown cables, especially for Power over Ethernet (PoE).
Straight-through Cable Key:
- For Computers and Routers:
- Sending Data: Pins 1 & 2 (Orange wires).
- Receiving Data: Pins 3 & 6 (Green wires).
- For Hubs and Switches:
- Sending Data: Pins 1 & 2 (Green wires).
- Receiving Data: Pins 3 & 6 (Orange wires).
⭐Twisted Pair Ethernet: Crossover Cables
Crossover Cables
Crossover cables are a type of Ethernet cable used primarily in older network environments and specialized connections. Although many modern devices have adopted Auto Medium Dependent Interface Crossover (Auto-MDI/MDIX) technology, which automatically adjusts the wiring configuration, understanding crossover cables is still valuable for working with legacy systems or in certain network setups.
Purpose and Usage
- Direct Device Connection: Crossover cables connect two computing devices directly. This is particularly useful for tasks such as:
- Administrative Access: Connecting an IT administrator’s laptop to an Enterprise device (like a server, switch, router, or hub) for updates, repairs, or configuration.
- Device Management: Connecting to the management port of Enterprise machines for system access and management.
- Other Connections: Crossover cables can also be used to connect:
- Two switches
- Two hubs
- A switch to a hub
- Two routers
- Two PCs
- A router to a PC
Identification
Color Coding: To distinguish a crossover cable from a straight-through cable, examine the color order of the twisted pairs at both ends of the cable.
For T-568-A Wiring Scheme:
- Endpoint 1:
- Pins 1 & 2: Green wires (sending data)
- Pins 3 & 6: Orange wires (receiving data)
- Endpoint 2:
- Pins 1 & 2: Orange wires (sending data)
- Pins 3 & 6: Green wires (receiving data)
For T-568-B Wiring Scheme:
- Endpoint 1:
- Pins 1 & 2: Orange wires (sending data)
- Pins 3 & 6: Green wires (receiving data)
- Endpoint 2:
- Pins 1 & 2: Green wires (sending data)
- Pins 3 & 6: Orange wires (receiving data)
The crossover configuration ensures that sending and receiving wires are matched correctly between two devices, which is necessary when both devices use the same wires for transmitting and receiving data.
- Endpoint 1:
Wiring Schemes
- Straight-through Cables: Typically use the T-568B wiring scheme.
- Crossover Cables: Utilize both T-568A and T-568B schemes to enable proper data transmission between devices with matching send/receive wires.
Crossover Cable Key
Endpoint 1:
- Pins 1 & 2: Green wires (sending data)
- Pins 3 & 6: Orange wires (receiving data)
Endpoint 2:
- Pins 1 & 2: Orange wires (sending data)
- Pins 3 & 6: Green wires (receiving data)
⭐The Data Link Layer:
1) Ethernet and MAC Addresses:
Ethernet is a foundational technology in computer networking, and understanding how it works with MAC addresses is crucial for troubleshooting and configuring network connections. Here’s a detailed breakdown of Ethernet, MAC addresses, and related concepts:
Ethernet Overview
Ethernet, a widely used networking technology, was first standardized in 1983. Despite its age, Ethernet remains relevant due to its adaptability and ongoing advancements. It provides a framework for transmitting data across network links, abstracting the physical layer to allow higher-level software to operate independently of the underlying hardware.
Key Concepts:
- Carrier Sense Multiple Access with Collision Detection (CSMA/CD): This protocol helps manage data transmission over a network segment where collisions might occur. Devices use CSMA/CD to detect whether the network is clear before sending data and to handle collisions by retransmitting after a random delay.
MAC Addresses
A MAC (Media Access Control) address is a unique identifier assigned to each network interface card (NIC) for the purpose of network communication.
Key Details:
Format: A MAC address is a 48-bit number, commonly represented as six groups of two hexadecimal digits (e.g.,
00:1A:2B:3C:4D:5E). Each pair of hexadecimal digits represents an octet (8 bits).Hexadecimal System: Uses 16 symbols (0-9 and A-F) to represent values. Each hex digit corresponds to 4 bits, so two hex digits represent an 8-bit byte.
Uniqueness: MAC addresses are designed to be globally unique. With 48 bits, there are or 281,474,976,710,656 possible addresses.
Structure:
Organizationally Unique Identifier (OUI): The first three octets (24 bits) of a MAC address are assigned to manufacturers by the IEEE. This helps identify the hardware manufacturer.
Device Identifier: The last three octets (24 bits) are assigned by the manufacturer, ensuring uniqueness within their range.
Addressing Types
Unicast:
- Definition: A one-to-one communication method where data is sent from one device to a specific, single destination device.
- Example: Sending an email to a specific recipient.
Multicast:
- Definition: A one-to-many communication method where data is sent from one device to a group of devices that have expressed interest in receiving it.
- Example: Streaming video to multiple users on a network.
Broadcast:
- Definition: A one-to-all communication method where data is sent from one device to all devices on the network segment.
- Example: Sending an ARP request to find the MAC address of a device with a specific IP address.
Error Checking
Cyclical Redundancy Check (CRC):
- Purpose: Ensures data integrity by detecting errors in transmitted Ethernet frames.
- Function: CRC involves appending a short, fixed-size checksum (CRC value) to the end of data frames. The receiver performs a similar calculation and compares the result with the checksum. If they match, the data is likely error-free; if not, the frame is discarded, and retransmission may be requested.
2) Unicast, Multicast, and Broadcast:
In Ethernet networks, data transmission can occur in different ways depending on the intended audience. Understanding these methods—unicast, multicast, and broadcast—is crucial for network management and troubleshooting. Here’s a breakdown of each type:
1. Unicast
Definition: Unicast communication involves sending data from one device to a specific, single destination device.
Addressing: In Ethernet, unicast frames are identified by their destination MAC address. The least significant bit (LSB) of the first octet in the MAC address is set to 0 for unicast addresses.
Example: If a computer wants to send a file to a specific server, it uses the server’s unique MAC address. The data frame is transmitted to all devices on the collision domain, but only the server with the matching MAC address processes it.
Characteristics:
- One-to-one communication.
- Efficient when communicating with a specific device.
- Reduces network congestion compared to broadcast.
2. Multicast
Definition: Multicast communication involves sending data from one device to multiple, but not all, devices on a network segment.
Addressing: Multicast frames use a MAC address where the LSB of the first octet is set to 1. However, multicast addresses are not fixed; devices can be configured to listen for specific multicast addresses based on the application’s requirements.
Example: Streaming video to a group of users on a network. The source device sends data to a multicast address, and only devices interested in that specific multicast group will process the data.
Characteristics:
- One-to-many communication.
- Reduces network traffic compared to broadcast since only interested devices receive the data.
- Devices must be configured to recognize and process multicast addresses.
3. Broadcast
Definition: Broadcast communication involves sending data from one device to all devices on a local network segment.
Addressing: Broadcast frames use a special destination MAC address where all 48 bits are set to 1 (i.e.,
FF:FF:FF:FF:FF:FF).Example: An ARP (Address Resolution Protocol) request to find the MAC address corresponding to a specific IP address is broadcasted to all devices on the network segment. Every device receives and processes the request, but only the device with the matching IP address responds.
Characteristics:
- One-to-all communication.
- Useful for network discovery and communication with all devices on a LAN.
- Can lead to network congestion if overused, as all devices process broadcast frames.
3) Dissecting an Ethernet Frame:
Understanding the structure of an Ethernet frame is fundamental for networking. An Ethernet frame encapsulates data being sent across a network and ensures that the data is correctly addressed and validated. Here’s a detailed breakdown of each part of an Ethernet frame:
1. Preamble (8 bytes / 64 bits)
- Purpose: Acts as a synchronization pattern for the receiving device’s clock and prepares the network interface for receiving the data frame.
- Structure:
- First 7 bytes: Alternating ones and zeros (10101010…).
- Last byte (Start Frame Delimiter, SFD): Signals the end of the preamble and the start of the actual frame data. It is represented as
10101011.
2. Destination MAC Address (6 bytes / 48 bits)
- Purpose: Specifies the hardware address of the intended recipient of the frame. It ensures that the data is delivered to the correct device.
- Format: A unique identifier for each network interface card (NIC) on the network.
3. Source MAC Address (6 bytes / 48 bits)
- Purpose: Indicates the hardware address of the sender of the frame. This helps the recipient device know who sent the data.
- Format: Similar to the destination MAC address, it's a unique identifier.
4. Ether-Type / Length Field (2 bytes / 16 bits)
Purpose: Defines the protocol used in the data payload (e.g., IPv4, IPv6). It can also indicate the length of the payload.
Format:
- Ether-Type: Specifies the protocol (e.g.,
0x0800for IPv4). - Length: In some frames, this field indicates the size of the payload (in bytes).
- Ether-Type: Specifies the protocol (e.g.,
Note: In the presence of a VLAN tag, the Ether-Type field is located after the VLAN header.
5. VLAN Tag (Optional, 4 bytes / 32 bits)
- Purpose: Used for Virtual LAN (VLAN) tagging, allowing multiple logical networks to operate over the same physical network infrastructure.
- Components:
- Tag Protocol Identifier (TPID): Indicates the presence of a VLAN tag.
- Tag Control Information (TCI): Includes VLAN ID and priority information.
6. Data Payload (46-1500 bytes)
- Purpose: Contains the actual data being transmitted. This includes higher-layer protocol data such as IP packets, TCP segments, etc.
- Range: The payload length varies between 46 and 1500 bytes. If the payload is smaller than 46 bytes, padding is added to meet the minimum frame size.
7. Frame Check Sequence (FCS) (4 bytes / 32 bits)
- Purpose: Contains a checksum value used for error checking. It ensures the integrity of the data by allowing the receiving device to verify if the frame was corrupted during transmission.
- Mechanism: Utilizes Cyclic Redundancy Check (CRC) to compute a checksum that represents the entire frame’s data. The receiving device performs its own CRC calculation and compares it with the FCS value. If they match, the frame is considered intact; if not, the frame is discarded.
⭐Module 1 Glossary:
Bit: The smallest unit of data in computing, representing a binary value of either 0 or 1.
Border Gateway Protocol (BGP): A protocol used by routers to exchange routing information and manage how data is routed between different networks.
Broadcast: A type of Ethernet transmission sent to all devices on a Local Area Network (LAN).
Broadcast Address: A special address used to broadcast data to all devices on a network, represented by all hexadecimal Fs (
FF:FF:FF:FF:FF:FF).Cable Categories: Classifications of network cables based on their physical characteristics and performance capabilities. Categories include copper and fiber cables.
Cables: Insulated wires that connect devices and enable data transmission.
Carrier-Sense Multiple Access with Collision Detection (CSMA/CD): A protocol that manages access to the network channel and detects collisions to prevent data transmission conflicts.
Client: A device that requests and receives data from a server.
Collision Domain: A network segment where data packets can collide if two devices transmit simultaneously.
Computer Networking: The practice of connecting computers and other devices to share resources and communicate.
Copper Cable Categories: Categories of twisted pair cables, such as Cat5, Cat5e, and Cat6, that differ in performance and data transmission rates.
Crosstalk: Interference caused by signals from one wire being picked up by another wire.
Cyclic Redundancy Check (CRC): A method for detecting errors in data transmission by using polynomial division to create a checksum.
Data Packet: A unit of data transmitted over a network link. In Ethernet, this is known as an Ethernet frame.
Data Link Layer: The layer responsible for defining a standard for data transmission between devices on the same network segment.
Destination MAC Address: The unique identifier for the intended recipient of an Ethernet frame.
Duplex Communication: The ability to send and receive data simultaneously (full duplex) or alternately (half duplex) across a network link.
Ethernet: A widely used protocol for sending data across network links.
Ethernet Frame: A structured format used to transmit data over an Ethernet network, containing fields like MAC addresses, payload, and CRC.
EtherType Field: A 16-bit field in an Ethernet frame that specifies the protocol used in the data payload.
Fiber Cable: Cables made of optical fibers that transmit data using light pulses, offering high-speed and long-distance communication.
Five Layer Model: A simplified networking model consisting of Physical, Data Link, Network, Transport, and Application layers.
Frame Check Sequence (FCS): A 32-bit checksum used for error-checking in Ethernet frames.
Full Duplex: Communication where both devices can send and receive data simultaneously.
Half-Duplex: Communication where devices can either send or receive data, but not both at the same time.
Hexadecimal: A base-16 numeral system used to represent data in a more compact form than binary.
Hub: A network device that broadcasts data to all connected devices within a collision domain.
Internet Protocol (IP): The protocol used for addressing and routing data across networks.
Internet Service Provider (ISP): A company that provides access to the Internet for consumers and businesses.
Internetwork: A network of networks connected through routers, such as the Internet.
Line Coding: A technique used to encode data for transmission over a network medium.
Local Area Network (LAN): A network that connects devices within a limited area, such as a home or office.
MAC (Media Access Control) Address: A unique identifier assigned to network interfaces for communication within a network segment.
Modulation: The process of varying a signal’s properties to encode data for transmission over a network medium.
Multicast Frame: An Ethernet frame sent to a specific group of devices identified by a multicast address.
Network Layer: The layer responsible for routing data between different networks through routers.
Network Port: A physical or virtual interface used to connect devices to a network.
Network Switch: A device that connects multiple devices within a network and uses MAC addresses to forward data only to the intended recipient.
Node: Any device connected to a network, such as computers, servers, and printers.
Octet: An 8-bit chunk of data, often used to describe sections of a MAC address or IP address.
Organizationally Unique Identifier (OUI): The first three octets of a MAC address, assigned to hardware manufacturers by IEEE.
OSI Model: A seven-layer model used to conceptualize network communication, including Physical, Data Link, Network, Transport, Session, Presentation, and Application layers.
Patch Panel: A device with multiple network ports used to manage and connect network cables.
Payload: The actual data being transmitted within an Ethernet frame, excluding headers and metadata.
Physical Layer: The layer that defines the physical connection between devices, including cables and hardware.
Preamble: The initial part of an Ethernet frame used for synchronization and preparation for data reception.
Protocol: A set of rules defining how data is transmitted and processed in a network.
Router: A device that forwards data between different networks and determines the best path for data to travel.
Server: A device that provides resources or services to clients on a network.
Simplex Communication: One-way communication where data travels in only one direction.
Source MAC Address: The unique identifier for the device that originated an Ethernet frame.
Start Frame Delimiter (SFD): The byte in the preamble that marks the beginning of the actual frame data.
Transmission Control Protocol (TCP): A connection-oriented protocol used for reliable data transmission.
Transport Layer: The layer responsible for end-to-end communication and data transfer between applications.
Twisted Pair Cable: A type of copper cable used for network connections, consisting of pairs of twisted wires.
Unicast Transmission: A type of Ethernet transmission intended for a single recipient.
User Datagram Protocol (UDP): A connectionless protocol used for fast, unreliable data transmission without acknowledgments.
Virtual LAN (VLAN): A network configuration technique that allows multiple logical networks to operate on the same physical infrastructure.
VLAN Header: Information in an Ethernet frame that indicates VLAN membership and configuration.
🚨Thanks for visiting classpdfindia✨
Welcome to a hub for 😇Nerds and knowledge seekers! Here, you'll find everything you need to stay updated on education, notes, books, and daily trends.
💗 Bookmark our site to stay connected and never miss an update!
💌 Have suggestions or need more content? Drop a comment below, and let us know what topics you'd like to see next! Your support means the world to us. 😍